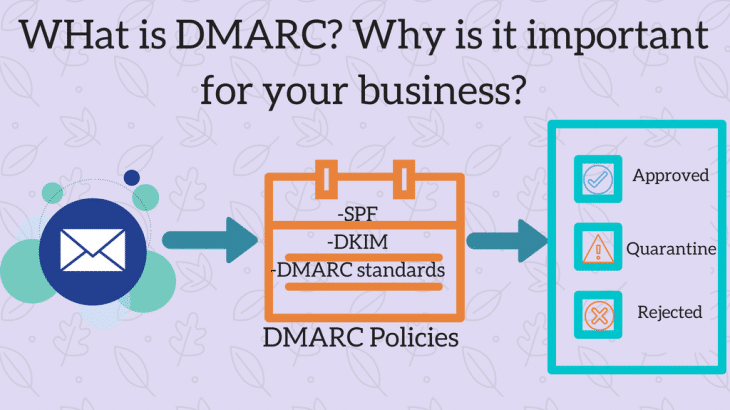
DMARC and why it is important for your business?
What is DMARC? DMARC (Domain-based Message Authentication, Reporting and Conformance) is a technology advancement in preventing email and domain spoofing. It ensures that emails go through a domain based check and then sent to the recipient. It uses DKIM and SPF standards along with additional standards of its own. It